A single data breach costs companies an average of $4.88 million. For 60% of small businesses, it’s a death sentence—they close within six months of an attack.
Your customer database. Financial records. Intellectual property. Employee information. Every byte of data your organization creates, stores, or processes is a target. Hackers don’t discriminate—they attack Fortune 500 companies and local businesses with equal fervor, seeking any weakness in your digital armor.
Last year alone, 3,205 publicly reported breaches exposed the personal information of 353 million people—a 78% jump from the previous year. Naturally, data security isn’t about installing antivirus software and hoping for the best anymore. It’s a systematic approach to protecting your digital assets from creation to deletion. It means building walls that actually hold, creating access controls that work, and having a plan when—not if—someone tries to break in.
Your Security, Our Assurance!
Don’t leave your digital assets at risk. Strengthen your defenses now by partnering with Kanerika
What is Data Security?
Data security is the practice of protecting digital information from unauthorized access, corruption, theft, or destruction throughout its entire lifecycle. It encompasses technical safeguards, administrative controls, and physical protections that work together to maintain data confidentiality, integrity, and availability.
The primary goal of data security is to defend against today’s growing spectrum of cyber threats—ransomware, malware, insider threats, social engineering, and human error—while enabling secure and efficient data utilization for business operations.
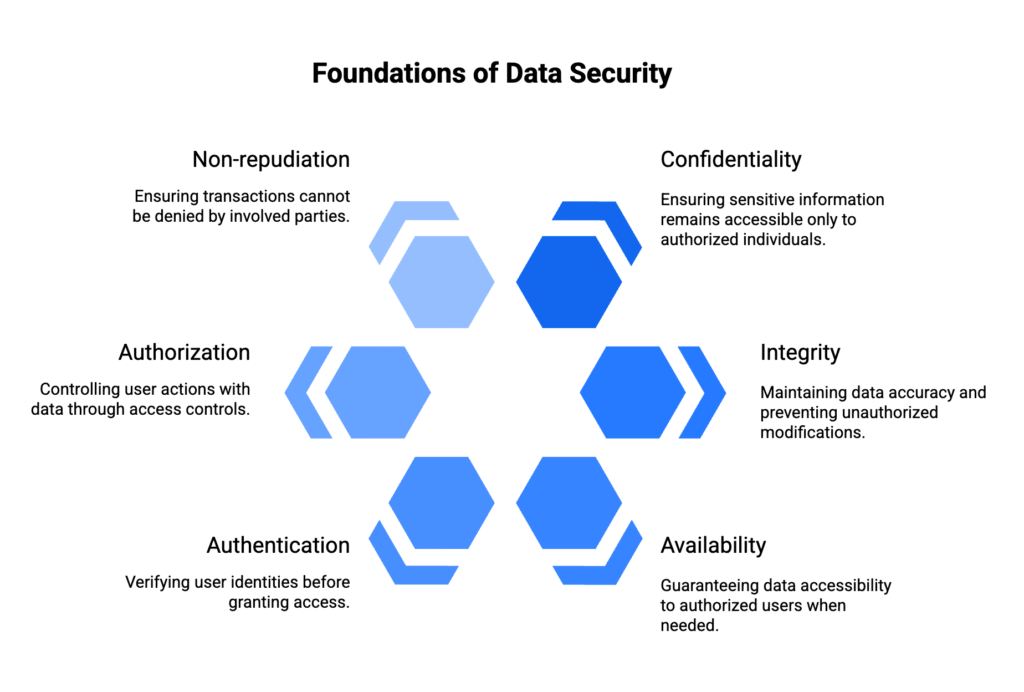
Key Principles of Data Security
- Confidentiality: Ensuring sensitive information remains accessible only to authorized individuals through access controls, encryption, and user authentication mechanisms.
- Integrity: Maintaining data accuracy, completeness, and trustworthiness by preventing unauthorized modifications and detecting any alterations to critical information.
- Availability: Guaranteeing that information systems and data remain accessible to authorized users when needed, even during security incidents or system failures.
- Authentication: Verifying the identity of users, devices, and systems before granting access to sensitive data or resources.
- Authorization: Controlling what authenticated users can do with data, implementing role-based access controls and the principle of least privilege.
- Non-repudiation: Ensuring that data transactions and communications cannot be denied by the parties involved, typically through digital signatures and audit trails.
Data Security vs Data Privacy
While deeply interconnected, data security and data privacy serve distinct but complementary purposes in protecting organizational information.
Data Security Focus Areas
It concentrates on how sensitive information is protected through:
- Firewalls and network security controls
- Data loss prevention (DLP) technologies
- Encryption and tokenization
- Access management systems
- Endpoint protection platforms
- Security monitoring and incident response
Data Privacy Focus Areas
However, data privacy addresses how personal information is collected, processed, stored, and shared:
- Consent management and user rights
- Data minimization and purpose limitation
- Cross-border data transfer regulations
- Individual access and deletion requests
- Privacy impact assessments
- Transparency and disclosure requirements
The Intersection
Privacy regulations like GDPR and CCPA mandate transparency in data usage while granting individuals control over their personal information. Data security measures support these requirements by ensuring only authorized personnel can access personally identifiable information (PII) and that this data is processed securely and compliantly.
In essence, data security protects the data; data privacy governs its use.
For individuals and businesses seeking greater control over their personal data exposure, Incogni offer automated tools to manage and remove personal information from internet.
Why Data Security Matters?
Organizations generate over 402.74 million terabytes of data daily, with the United States alone housing more than 5000 data centers. This massive data volume represents tremendous business value—and equally significant risk exposure.
Direct Financial Impact:
- Average data breach cost: $4.88 million globally
- Healthcare breach cost: $11.05 million average
- Ransomware attack cost: $5.13 million average
- Lost business cost: $1.90 million per breach
Operational Consequences:
- Business disruption and downtime
- Productivity losses during incident response
- System rebuilding and data recovery costs
- Increased cybersecurity insurance premiums
Regulatory Compliance Requirements
The global regulatory landscape continues expanding as data becomes increasingly critical to business operations. Major frameworks include:
- GDPR: Up to 4% of annual global revenue in fines
- CCPA/CPRA: Penalties up to $7,500 per violation
- HIPAA: Fines ranging from $137-$2.067 million
- PCI DSS: Fines up to $500,000 per incident
- SOX: Criminal penalties including imprisonment
In 2024, GDPR enforcement alone resulted in EUR 1.2 billion in fines, demonstrating regulators’ commitment to data protection accountability.
Competitive Advantage and Trust
Robust data security creates measurable business advantages:
- Customer Trust: 86% of consumers care about data privacy and choose businesses with strong security practices
- Partner Confidence: Vendors and partners require security certifications for business relationships
- Market Differentiation: Security leadership becomes a competitive advantage in privacy-conscious markets
- Innovation Enablement: Secure foundations support digital transformation and emerging technology adoption
Types of Data Security Threats
External Cyber Threats
- Ransomware Attacks: Sophisticated encryption-based extortion schemes targeting critical business systems and data. Modern ransomware often includes data exfiltration, threatening public disclosure if ransom demands aren’t met.
- Advanced Persistent Threats (APTs): Long-term, stealthy campaigns targeting specific organizations to steal intellectual property, financial data, or sensitive information over extended periods.
- Phishing and Social Engineering: Manipulating human psychology to trick employees into revealing credentials, installing malware, or providing unauthorized access to systems and data.
- Malware and Virus Attacks: Malicious software designed to infiltrate systems, steal data, disrupt operations, or create backdoors for future attacks.
- Distributed Denial of Service (DDoS): Overwhelming systems with traffic to disrupt availability and potentially mask other malicious activities.
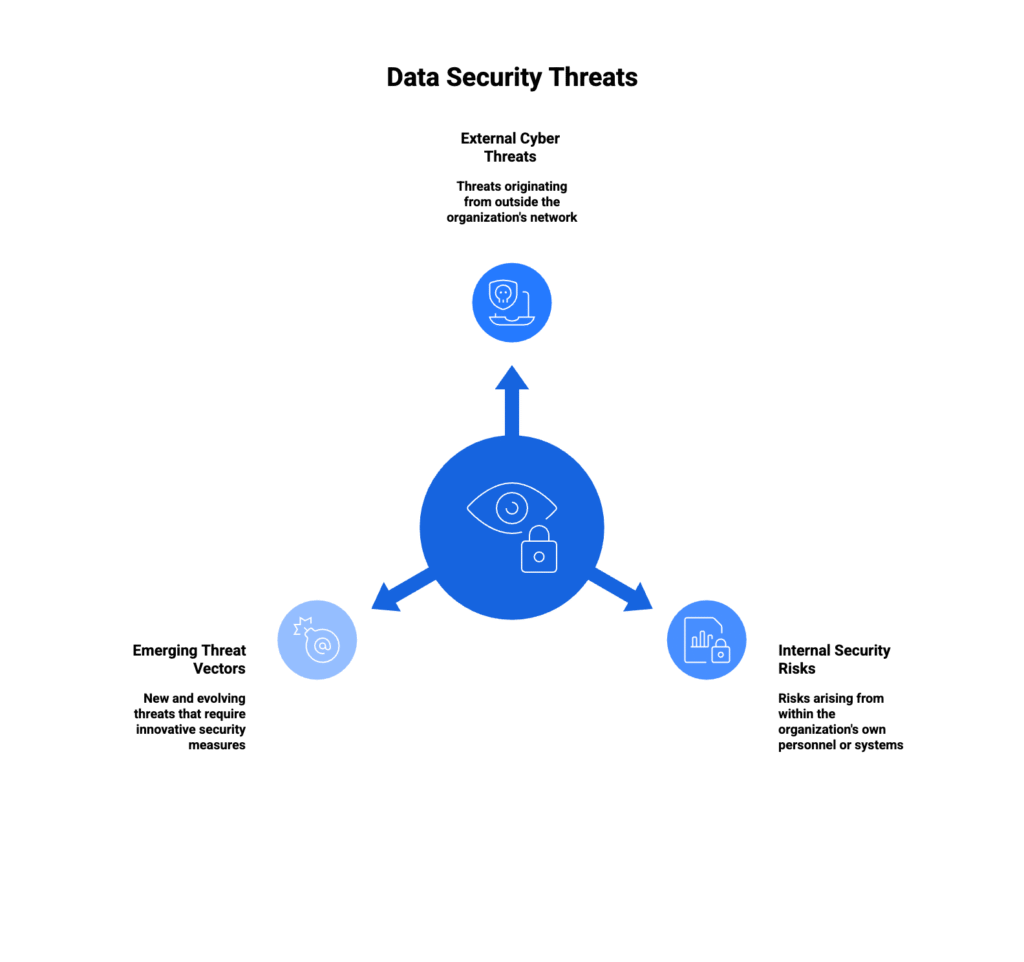
Internal Security Risks
- Insider Threats: Malicious or negligent actions by employees, contractors, or business partners with legitimate access to organizational systems and data.
- Human Error: Accidental data exposure through misconfigured systems, misdirected emails, lost devices, or inadequate security practices.
- Privilege Abuse: Authorized users exceeding their access permissions or using legitimate access for unauthorized purposes.
- Third-Party Vulnerabilities: Security weaknesses in vendor systems, software supply chains, or partner networks that create indirect exposure risks.
Emerging Threat Vectors
- AI-Powered Attacks: Machine learning algorithms used to automate vulnerability discovery, create convincing deepfakes, and enhance social engineering campaigns.
- IoT Device Exploitation: Compromising Internet of Things devices to access networks, steal data, or launch larger attacks against connected infrastructure.
- Cloud Misconfigurations: Improperly configured cloud services exposing sensitive data through inadequate access controls or public storage buckets.
- Supply Chain Attacks: Targeting trusted software vendors or service providers to gain access to their customers’ systems and data.
Data Security Measures and Technologies
Encryption and Data Protection
- Encryption at Rest: Protecting stored data using advanced encryption algorithms like AES-256, ensuring data remains secure even if physical storage devices are compromised or stolen.
- Encryption in Transit: Securing data movement between systems using protocols like TLS 1.3, preventing interception and manipulation during transmission across networks.
- End-to-End Encryption: Providing complete protection from sender to recipient, ensuring only authorized parties possess the decryption keys necessary to access sensitive information.
- Key Management: Implementing centralized key generation, distribution, rotation, and destruction procedures to maintain encryption effectiveness and prevent unauthorized access.
Advanced Authentication Systems
- Multi-Factor Authentication (MFA): Combining multiple verification methods including knowledge factors (passwords), possession factors (tokens), and inherence factors (biometrics) for enhanced security.
- Biometric Authentication: Utilizing unique physical characteristics like fingerprints, facial recognition, iris scanning, and voice patterns for high-security identification and access control.
- Single Sign-On (SSO): Streamlining user access across multiple applications while maintaining centralized authentication and security policy enforcement.
- Privileged Access Management (PAM): Controlling and monitoring administrative access to critical systems through just-in-time access, session recording, and automated credential rotation.
How to Protect Sensitive Data with Microsoft Purview Data Loss Prevention
Microsoft Purview DLP provides robust tools to detect, protect, and manage sensitive information across various platforms such as endpoints, Office 365, OneDrive, SharePoint, Microsoft Teams, and Microsoft 365 Copilot.
Data Protection Technologies
- Data Masking: Obscuring sensitive data elements by replacing them with fictitious yet structurally similar information, enabling development and testing without privacy regulation violations.
- Data Loss Prevention (DLP): Monitoring, detecting, and preventing unauthorized data transfers across email, web, removable media, and cloud applications through content inspection and policy enforcement.
- Secure Data Deletion: Ensuring complete data overwriting and irrecoverability when retiring storage devices or removing sensitive information from systems.
- Data Tokenization: Replacing sensitive data with unique identification symbols while maintaining data utility for processing without exposing actual values.
Top Data Security Tools
Securing business data isn’t only about blocking hackers—it’s also about controlling access, ensuring compliance, and managing information responsibly. Several enterprise tools stand out in this space:
1. Databricks
Databricks offers a secure platform for managing and analyzing large volumes of data. With features like role-based access control and audit logging, it helps organizations protect sensitive information while still enabling teams to collaborate.

2. Collibra
Collibra is widely used for data governance. It ensures that only the right people have access to the right data. By creating a clear framework for data ownership, quality, and compliance, Collibra reduces the risk of accidental leaks or misuse.
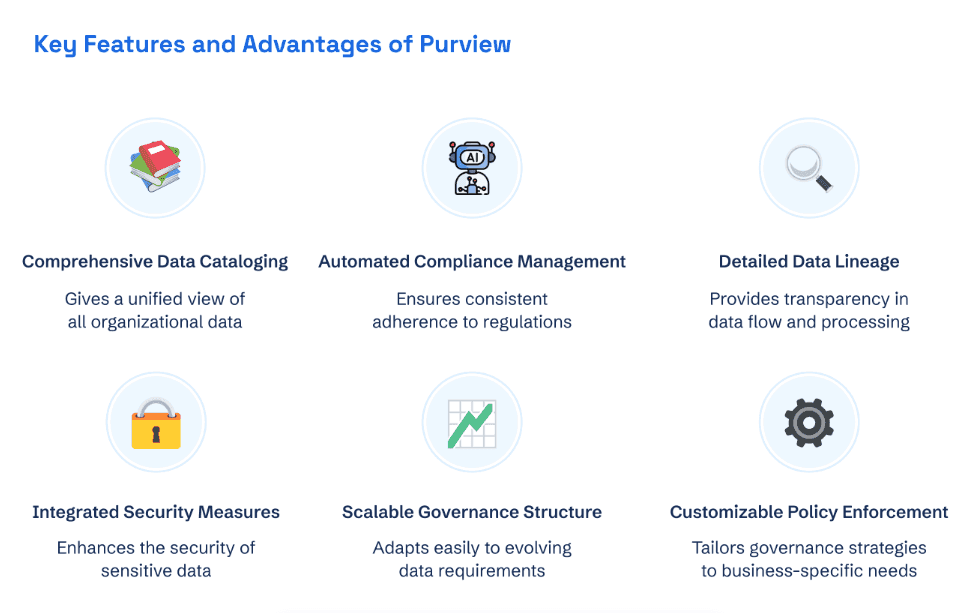
3. Microsoft Purview
Purview provides unified data governance across on-premises, cloud, and SaaS platforms. Its strong classification, lineage tracking, and regulatory compliance tools help businesses keep data secure while meeting privacy requirements.
4. Informatica
Informatica combines data integration with governance and security controls. It provides encryption, masking, and monitoring to safeguard sensitive assets across systems.
Together, these tools give businesses visibility, control, and protection. Instead of treating security as an add-on, they embed it directly into how data is stored, shared, and used.
Data Security and Compliance
Global Regulatory Landscape
The regulatory environment continues evolving as data becomes more critical to business operations and more valuable to cybercriminals:
- General Data Protection Regulation (GDPR): European Union’s comprehensive privacy law affecting any organization processing EU citizens’ personal data, with fines up to 4% of annual global revenue or €20 million, whichever is higher.
- California Consumer Privacy Act (CCPA) / California Privacy Rights Act (CPRA): Provides California residents with enhanced privacy rights including data access, deletion, and opt-out of sale, with penalties up to $7,500 per intentional violation.
- Health Insurance Portability and Accountability Act (HIPAA): Protects patient health information in healthcare organizations through detailed security and privacy requirements, with fines ranging from $137 to $2.067 million.
- Payment Card Industry Data Security Standard (PCI DSS): Mandates specific security measures for organizations handling credit card information, with non-compliance fines up to $500,000 per incident.
- Sarbanes-Oxley Act (SOX): Requires public companies to maintain accurate financial records and implement internal controls, with criminal penalties including imprisonment for executives.
Emerging Global Regulations
- Digital Personal Data Protection Act (India): India’s comprehensive privacy law affecting organizations processing Indian citizens’ personal data.
- Personal Information Protection Law (PIPL) (China): China’s data protection regulation governing personal information processing with significant extraterritorial reach.
- Lei Geral de Proteção de Dados (LGPD) (Brazil): Brazil’s general data protection law modeled after GDPR with similar requirements and penalties.
Data Analytics in the Automotive Industry: How Top Brands Stay Ahead
From virtual assistants to generative design, data analytics in the automotive industry is enabling companies to blend innovation with comfort and safety.
Compliance Implementation Strategy
- Gap Analysis: Systematic evaluation of current practices against regulatory requirements to identify areas needing improvement or additional controls.
- Documentation Requirements: Maintaining comprehensive records of data processing activities, security measures, breach notifications, and compliance demonstrations.
- Regular Audits: Internal and external assessments to validate ongoing compliance and identify potential violations before regulatory examinations.
- Cross-Border Data Transfers: Implementing appropriate safeguards for international data movements including adequacy decisions, standard contractual clauses, and binding corporate rules.
Network and Endpoint Security
- Next-Generation Firewalls: Advanced network protection combining traditional firewall capabilities with application awareness, intrusion prevention, and advanced threat detection.
- Endpoint Detection and Response (EDR): Continuous monitoring and analysis of endpoint activities to detect and respond to suspicious behaviors and potential security incidents.
- Network Segmentation: Isolating critical systems and data through micro-segmentation, limiting lateral movement during security breaches and containing potential damage.
- Intrusion Detection and Prevention Systems (IDS/IPS): Real-time monitoring of network traffic and system activities to identify and block malicious activities automatically.
Kanerika: Your Ideal Data Security Partner
Why Choose Kanerika for Data Security
When it comes to keeping your data safe and well-governed, Kanerika brings clarity, structure, and compliance front and center. Three core offerings—KanGovern, KANComply, and KanSecure—work together to give you peace of mind:
- KanGovern lays the groundwork for smart data governance. It helps you discover, catalog, and manage your data assets efficiently, cutting through silos and giving your team visibility and control.
- KanComply ensures your operations line up with global laws and industry rules. With support for over 360 international regulations, it guides you in managing compliance head‑on, not as an afterthought.
- KanGuard focuses on securing your data with enforcement, policy-driven protection, and risk monitoring. It builds a safe environment where only the right people and systems can access sensitive data.
By combining those three, Kanerika doesn’t just protect your data—it makes managing, understanding, and complying with it simpler, smarter, and more measurable. That kind of setup pays off: fewer risks, clearer policies, and stronger confidence for your team—and your leadership.
Case Study: Kanerika’s Microsoft Purview Implementation
Kanerika successfully implemented Microsoft Purview for a leading enterprise client, delivering measurable improvements in data governance, security, and operational efficiency. This isn’t theory — it’s execution.
Client Challenge:
The organization struggled with fragmented data tools, manual classification processes, and siloed environments that compromised compliance and collaboration.
Kanerika’s Solution:
Leveraging Microsoft Purview, Kanerika deployed:
- Automated data discovery using Purview’s Data Map
- Sensitive data classification with improved visibility and control
- End-to-end data lineage from source systems to analytics in the Lakehouse
Outcome Delivered:
- 30% boost in reporting efficiency
- 25% reduction in audit time
- 90% increase in informed decision-making
Your Security, Our Assurance!
Don’t leave your digital assets at risk. Strengthen your defenses now by partnering with Kanerika
FAQs
What is meant by data security?
Data security is the practice of protecting digital information from unauthorized access, use, disclosure, disruption, modification, or destruction. It involves a multi-layered approach, encompassing technical safeguards, policies, and procedures. Ultimately, it’s about ensuring data integrity and confidentiality, preserving trust, and mitigating risks. The goal is to maintain control and accountability over sensitive information.
What are the 3 types of data security?
Data security isn’t neatly divided into just three types, but we can categorize it broadly. Think of it as protecting data’s *confidentiality* (keeping it secret), its *integrity* (ensuring it’s accurate and unaltered), and its *availability* (making sure it’s accessible when needed). These three pillars work together to form a comprehensive security strategy. Failing in one weakens the whole system.
What are the four elements of data security?
Data security hinges on four key pillars: Confidentiality (keeping data secret), Integrity (ensuring data accuracy and trustworthiness), Availability (guaranteeing timely access to data when needed), and Authenticity (verifying the origin and identity of data). These work together to protect information’s value and reliability. Neglecting any one weakens the overall security posture.
What are the 3 principles of data security?
Data security rests on three core pillars: Confidentiality (keeping data secret from unauthorized access), Integrity (ensuring data accuracy and trustworthiness), and Availability (guaranteeing timely and reliable access for authorized users). These principles work together to create a robust security posture. Ignoring any one weakens the overall protection.
What are the benefits of data security?
Data security protects your valuable information from theft, damage, or misuse, safeguarding your reputation and avoiding costly legal repercussions. It ensures business continuity by preventing disruptions caused by breaches. Ultimately, strong data security fosters trust with customers and partners, building a stronger and more resilient organization.
What do you mean by data protection and security?
Data protection and security means safeguarding your information from unauthorized access, use, disclosure, disruption, modification, or destruction. It’s a multi-layered approach encompassing technical measures (like encryption) and procedural safeguards (like access controls). Ultimately, it’s about ensuring data integrity and confidentiality while maintaining its availability when needed. Think of it as building a strong, multi-layered castle wall around your valuable information.
What do you mean by data security measure?
Data security measures are the safeguards we put in place to protect your information from unauthorized access, use, disclosure, disruption, modification, or destruction. Think of them as a multi-layered defense system, encompassing everything from strong passwords and encryption to physical security and employee training. The goal is to maintain confidentiality, integrity, and availability of your data. These measures adapt constantly to evolving threats.
Who is responsible for data security?
Data security is a shared responsibility. Ultimately, the organization owning the data bears the primary burden, encompassing policy, infrastructure, and oversight. However, every individual with access to that data – from employees to third-party vendors – shares accountability for its safe handling and protection. Failure at any level compromises the entire system.